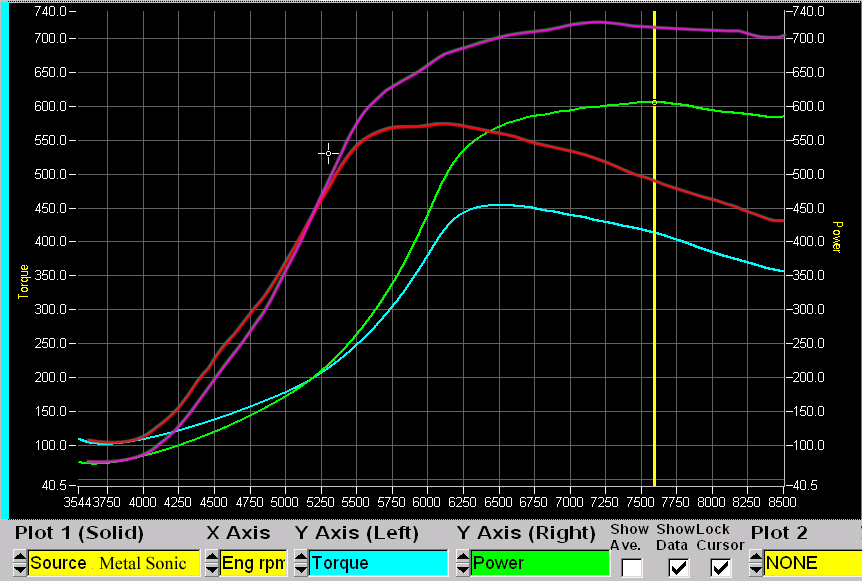
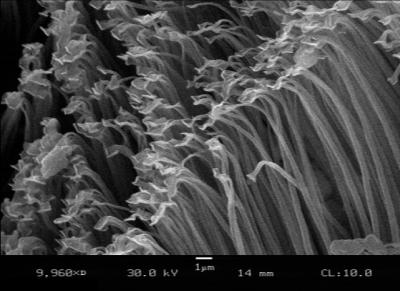
CCAM Rethreader Unit
Bringing together so many diverse populations of the multiverse causes some very strange dilemmas. Little can be assumed as ‘normal’ between race or even culture, militaristic or fighting dependencies among those topics. As a result, there is a shortage in some fields as to what is a Marshalship ‘standard’ to solve any giving dilemma in gearing.
Fairly recently was an occurrence that pointed out one such lack. The current standard H.E.V. (Hazardous Environment Suit) was designed around the concept of exploration and scientific study. Unfortunately, when placed into combat, it doesn’t live up to expectations. The mask is too strongly fitted, shattering under any real pressure, and the bulk of the suit itself restrains any real sense of mobility.
The CCAM (Complete Coverage and Monitoring) Rethreader Unit was designed as a compromise to this, and was later given further functionality. The unit itself is a belt, the buckle chamber being the storage space for the nano-threaders that do a bulk of the work, as well as the Lycra mixture which serves as the main material.

When activated, either via datapad or switch along the belt’s backing, the unit will enter one of a few customizable modes, threading an entire body glove out of the storage unit over the user regardless of prior clothing. The main purpose of the created suit is biological protection. The material threaded will protect against skin contact drugs or gases, radiation, and most things of that sort. Likewise, one of its modes may be threaded with a hood capable of fitting to the standard Marshalship re-breather unit, should full closure be deemed necessary. It does lose some functionality when compared to a standard H.E.V. unit, the two biggest concerns being that is does not have the necessary complexity to regulate temperature inside, nor does it have the hardware capable for emergency oxygen storage.
Its perks, however, are enough to justify its use. First off, it is extremely unrestricted, hindering combat mobility by almost nothing. Second, the very nature of how the suit creates itself also allows it to also repair itself. When a breach in the suit’s lining is detected, the same threaders that constructed it will re-weave the wounded area. This means suits will only have a narrow window of potential contamination, should attackers try to cause some trap around chemical exposure. Related to this is the perk of customizability.
****The image below shows three adaptations: the volunteer in their casual attire , one of a robe woven by the rethreader unit over her clothing, and one of a body glove fitted beneath, hardly visible except on exposed areas****
Customization allows the unit to remain ‘hidden’ against potential attackers. It can remain in a passive mode, unwoven, or programmed to weave as the users usual clothing, or remain as an active body glove beneath said clothing constantly. All up to the individual owner. Likewise, should the unit ever be compromised? It has a defensive measure. Unless the remote trigger is disabled, it can enter emergency mode via owner’s datapad, threading to entangle any would-be-thieves.
A final functionality was added to the unit after further discussion. The Marshalship currently has no passive monitoring system for combatants on the field. Teams rely on their own communication and any medic’s perceptions to have their injuries spotted and treated with the necessary expediency. A realization occurs with that thought, that this suit already encompasses an individual, and likewise is able to detect fractures or damage to its structure. Therefore, a medic with the capability to monitor suits is very close to monitoring every individual.
As a result of this thinking, a transmission unit has been fitted to the belt’s hardware, and I’ve created a datapad UI to go along with it. The medic with the software will receive a verbal warning (prioritized by severity of damage point, if multiple come in at once) of whose suit has been breached, and if they have the moment to do so mid-combat, also have the ability to then check visual specifics with a read out on their screen.

Everyone will be encouraged to carry one of these belts. As mentioned, every precaution necessary has been taken to try and ensure that every individual’s style or comfort has been accounted for, even visually, and not only will it offer you protection from some often unseen threats, but it will also make your medic’s job easier, ensuring they can treat you and others with better efficiency and awareness.